THANK YOU FOR SUBSCRIBING
How Big data and Machine Learning can prevent cyber breaches
Every year there are thousands of breach reports, that result in billions of records of crucial data being exposed. With prominent adoption of Internet of Things (IoT) and BYOD in companies, there has been an increase in cyber attacks also.
By
Apac CIOOutlook | Monday, February 25, 2019
Stay ahead of the industry with exclusive feature stories on the top companies, expert insights and the latest news delivered straight to your inbox. Subscribe today.
Every year there are thousands of breach reports, that result in billions of records of crucial data being exposed. With prominent adoption of Internet of Things (IoT) and BYOD in companies, there has been an increase in cyber attacks also. But the solution to this problem is also provided by technology itself. Using big data and Artificial intelligence tools like machine learning can help predict suspicious activities and vulnerabilities.
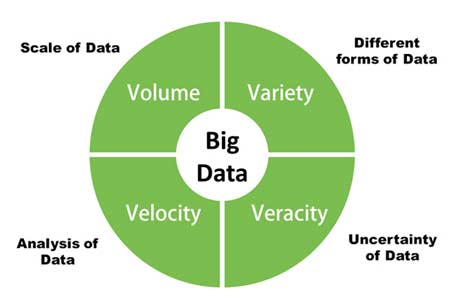
Bigdata
Big data enables automated risk management, threat visualization, and predictive analytics. By leveraging big data technology’s capability of processing high volume and variety of data with high velocity, companies can defend themselves from attacks by understanding their vulnerabilities and also behavioral patterns to help security operations spot anomalies.
Major anti-virus and cybersecurity vendors use big data to train their systems on the massive volumes of malware and known attack paths that they have previously collected. This enables companies to identify patterns to spot attacks that have never been seen before.
Using big data, penetration testing can be simulated. It is malware attack against a company’s computer systems and network to check for exploitable vulnerabilities. It is a mock-drill exercise to test the capabilities and existing analytics solutions. Penetration testing has become essential to protect IT infrastructure and business data.
Machine learning
Machine Learning is used to introduce intelligence to an organization’s first level of defense against cyber threats to all major categories of security tasks like prediction, prevention, detection, response, and monitoring. Feeding the vast pools of data collected by companies into machine learning algorithms, it can detect the root cause of the attack and also fix those detected anomalies in the network.
Blockchain
All the data stored on blockchain can be neither manipulated nor erased by design. The decentralized quality of blockchain dramatically increases the cost of breaching blockchain-based networks, hackers no longer can find a single point of entry or can they access any repositories of data in case they do get in. This feature of blockchain is the main reasons why enterprises are now considering it as a data privacy solution.
Blockchain technology is used to attain real-time secure data transmissions and also ensure timely communication between devices.
Hackers can get access to the connection between website name and IP address. They can use the company’s websites, divert people to scam websites, or just suspend the website. The current solution to such issues is to tail log files and enable real-time alerts for suspicious activities.
Because Blockchain is decentralized, it will be difficult for hackers to exploit single points of vulnerability. Company’s domain information can be stored immutably on a distributed ledger, and the connection can be powered by using blockchain.
See Also: